Establishing a secure remote connection to your Raspberry Pi using SSH is one of the most efficient ways to manage and interact with your device from anywhere in the world. Whether you're new to Raspberry Pi or an experienced developer, understanding how SSH operates and how to configure it is essential for anyone working with this versatile hardware. This guide will walk you through everything you need to know about SSH remote connections, from the basics to advanced configurations, ensuring you have the skills to manage your projects effectively.
In today's digital landscape, the ability to access devices remotely has become indispensable for both personal and professional projects. Whether you're managing a home server, configuring IoT devices, or running a web application, the ability to control your Raspberry Pi remotely is invaluable. SSH (Secure Shell) offers a secure and dependable method to achieve this, ensuring your data remains protected while providing seamless connectivity. This article will delve into the intricacies of SSH remote connections on Raspberry Pi, equipping you with the knowledge and confidence to implement SSH effectively.
Table of Contents
- Understanding SSH
- Exploring Raspberry Pi
- Setting Up SSH on Raspberry Pi
- Connecting to Raspberry Pi via SSH
- Troubleshooting Common Issues
- Enhancing SSH Security
- Advanced SSH Configurations
- Practical Use Cases for SSH on Raspberry Pi
- Optimizing SSH Performance
- Frequently Asked Questions
Understanding SSH
SSH, or Secure Shell, is a robust network protocol that enables users to securely access and manage remote devices over an encrypted connection. It provides a reliable framework for executing commands, transferring files, and managing system configurations without compromising security. SSH is widely adopted across various platforms, including Linux, macOS, and Windows, making it a universal solution for remote access.
Read also:Does Jonny Lee Miller Have Tattoos
Why Choose SSH for Remote Connections?
SSH offers numerous advantages over other remote access methods, making it a preferred choice for many users:
- Encryption: All data transmitted through SSH is encrypted, ensuring confidentiality and integrity of the information.
- Authentication: SSH supports multiple authentication methods, including passwords and public key authentication, enhancing security and reducing the risk of unauthorized access.
- Portability: SSH clients and servers are available for almost every operating system, making it versatile and accessible across different environments.
- Command Execution: SSH allows you to run commands on remote devices as if you were physically present, streamlining workflows and improving efficiency.
For Raspberry Pi users, SSH is particularly advantageous because it allows you to manage your device without needing a monitor, keyboard, or mouse. This makes it ideal for headless setups, where minimal hardware interaction is required.
Exploring Raspberry Pi
The Raspberry Pi is a compact, affordable computer designed to promote learning about computing and developing hardware projects. It supports a variety of operating systems, including Raspbian, Ubuntu, and others, and is widely used in education, home automation, and professional environments. Its versatility and affordability have made it a favorite among hobbyists and professionals alike.
Key Features of Raspberry Pi
- Compact Size: Raspberry Pi is lightweight and portable, making it an excellent choice for embedded systems and portable projects.
- Versatile Interfaces: It supports USB, HDMI, Ethernet, and GPIO pins, enabling a wide range of applications, from media centers to robotics.
- Open Source: The Raspberry Pi ecosystem is built around open-source software, encouraging innovation, collaboration, and customization.
Connecting to a Raspberry Pi via SSH enhances its usability by allowing remote management. This is especially beneficial for projects that require minimal hardware interaction, such as remote servers or IoT devices.
Setting Up SSH on Raspberry Pi
Enabling SSH on your Raspberry Pi is a simple process that can be completed in just a few steps. The exact steps may vary slightly depending on your operating system, but the core principles remain consistent across all setups.
Step 1: Enable SSH
To enable SSH on a Raspberry Pi running Raspbian, follow these straightforward steps:
Read also:Jeff Carriveau
- Open the Raspberry Pi Configuration tool by typing
sudo raspi-configin the terminal. - Navigate to the "Interfacing Options" menu and select it.
- Choose "SSH" from the list and enable it when prompted.
Alternatively, you can manually enable SSH by creating an empty file named "ssh" on the boot partition of your Raspberry Pi's SD card. This method is especially useful if you're setting up a headless Raspberry Pi without a monitor or keyboard.
Step 2: Configure Network Settings
Ensure your Raspberry Pi is connected to the same network as your client device. To check the IP address, run ifconfig or ip addr in the terminal. Note down the IP address, as you'll need it to establish the SSH connection.
Connecting to Raspberry Pi via SSH
Once SSH is enabled and your Raspberry Pi is connected to the network, you can establish a remote connection using an SSH client. The process varies slightly depending on your operating system.
Using SSH on Linux and macOS
Linux and macOS come with built-in SSH clients, making the connection process straightforward. To connect, open a terminal and type:
ssh pi@
Replace
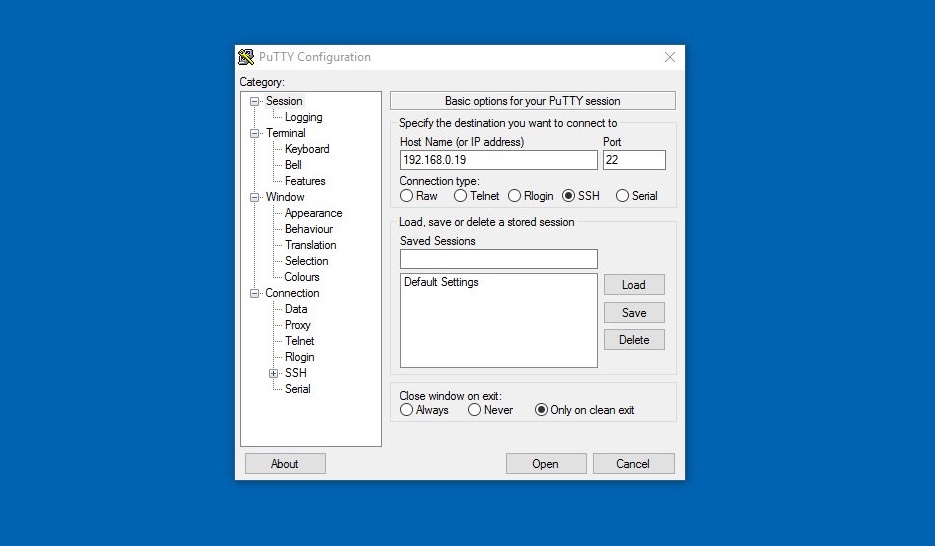
Using SSH on Windows
Windows 10 includes an SSH client by default, but you can also use third-party tools like PuTTY for a graphical interface. To connect using the command line, follow the same syntax as Linux and macOS.
Troubleshooting Common Issues
While SSH is generally reliable, issues may arise due to misconfigurations or network problems. Below are some common troubleshooting tips to help you resolve these issues:
- Connection Refused: Ensure SSH is enabled and verify that your Raspberry Pi is connected to the network.
- Incorrect IP Address: Double-check the IP address and confirm that the device is reachable from your network.
- Authentication Failure: Confirm that the username and password are correct. Consider using public key authentication for enhanced security and convenience.
Enhancing SSH Security
While SSH provides a secure connection, additional measures can further enhance its security:
1. Change Default Credentials
Modify the default "pi" username and "raspberry" password to prevent unauthorized access. Using strong, unique credentials is a crucial step in securing your Raspberry Pi.
2. Use Public Key Authentication
Public key authentication eliminates the need for passwords, reducing the risk of brute-force attacks. This method involves generating a key pair and configuring your Raspberry Pi to accept the public key.
3. Limit Access
Restrict SSH access to specific IP addresses or subnet ranges by configuring the firewall or SSH server settings. This ensures that only trusted devices can connect to your Raspberry Pi.
Advanced SSH Configurations
For more advanced users, SSH offers numerous configuration options to tailor its behavior to your specific needs:
Custom SSH Port
Changing the default SSH port (22) to a non-standard port can deter automated attacks. To do this, edit the /etc/ssh/sshd_config file and restart the SSH service to apply the changes.
Tunneling
SSH tunneling allows you to securely forward traffic between devices, enabling remote access to services behind firewalls. This is particularly useful for accessing databases or other services that are not directly exposed to the internet.
Practical Use Cases for SSH on Raspberry Pi
SSH has a wide range of applications in Raspberry Pi projects, enhancing its functionality and usability:
- Headless Setup: Manage your Raspberry Pi without a monitor or keyboard, making it ideal for remote servers or IoT devices.
- Remote Monitoring: Monitor system performance, logs, and other metrics from anywhere, ensuring your projects run smoothly.
- File Transfers: Use SCP or SFTP to transfer files securely between devices, simplifying data management and backups.
Optimizing SSH Performance
To improve SSH performance, consider the following tips:
Compression
Enable compression in the SSH configuration to reduce data transfer times over slow or unstable connections. This can significantly enhance the efficiency of your remote sessions.
Connection Reuse
Use SSH multiplexing to reuse existing connections, reducing latency for subsequent sessions. This is especially beneficial when you frequently connect to the same device.
Frequently Asked Questions
Here are some common questions about SSH and Raspberry Pi:
Can I use SSH on any operating system?
Yes, SSH clients are available for almost every operating system, including Windows, macOS, and Linux. This makes SSH a versatile and accessible solution for remote access.
Is SSH secure?
SSH is highly secure when configured correctly. Always use strong passwords, enable public key authentication, and follow best practices to enhance security and protect your device from potential threats.
Can I connect to Raspberry Pi from the internet?
Yes, but ensure proper security measures are in place, such as using a firewall, enabling two-factor authentication, and limiting access to trusted IP addresses. This helps protect your Raspberry Pi from unauthorized access when exposed to the internet.
Conclusion
SSH remote connections for Raspberry Pi are a powerful tool that simplifies remote management and enhances project flexibility. By following the steps outlined in this guide, you can set up, secure, and optimize SSH connections for your Raspberry Pi projects. Always adhere to best practices and continuously update your knowledge to stay ahead of potential security threats.
We encourage you to share your experiences or ask questions in the comments section below. For more in-depth guides and tutorials, explore our other articles on Raspberry Pi and related technologies. Happy coding and connecting!