In today's highly interconnected world, establishing secure connections for remote IoT Virtual Private Clouds (VPCs) has become a cornerstone of robust network security. As businesses and individuals increasingly rely on Internet of Things (IoT) devices, safeguarding these devices and their associated data has never been more critical. This article explores strategies, technologies, and best practices for securely connecting remote IoT networks within Virtual Private Clouds (VPCs).
With the rise of remote work and distributed systems, organizations face mounting challenges in ensuring the integrity, confidentiality, and availability of their data. IoT devices, often deployed in remote locations, add an additional layer of complexity to network security. This guide aims to provide actionable insights into securely connecting remote IoT VPC environments while maintaining compliance and mitigating risks.
Whether you're an IT professional, a business owner, or someone interested in enhancing cybersecurity, this article offers valuable information to help you navigate the intricacies of securing IoT devices in cloud environments. Let's explore the details together.
Read also:Sara Tancredi
Table of Contents
- Understanding IoT VPC
- The Importance of Secure Connections
- IoT VPC Architecture
- Key Security Challenges
- Best Practices for Secure Connections
- Technologies for Securing IoT VPC
- Securing Data Transmission
- Monitoring and Management
- Compliance and Regulations
- Future Trends in IoT Security
- Conclusion and Next Steps
Understanding IoT VPC
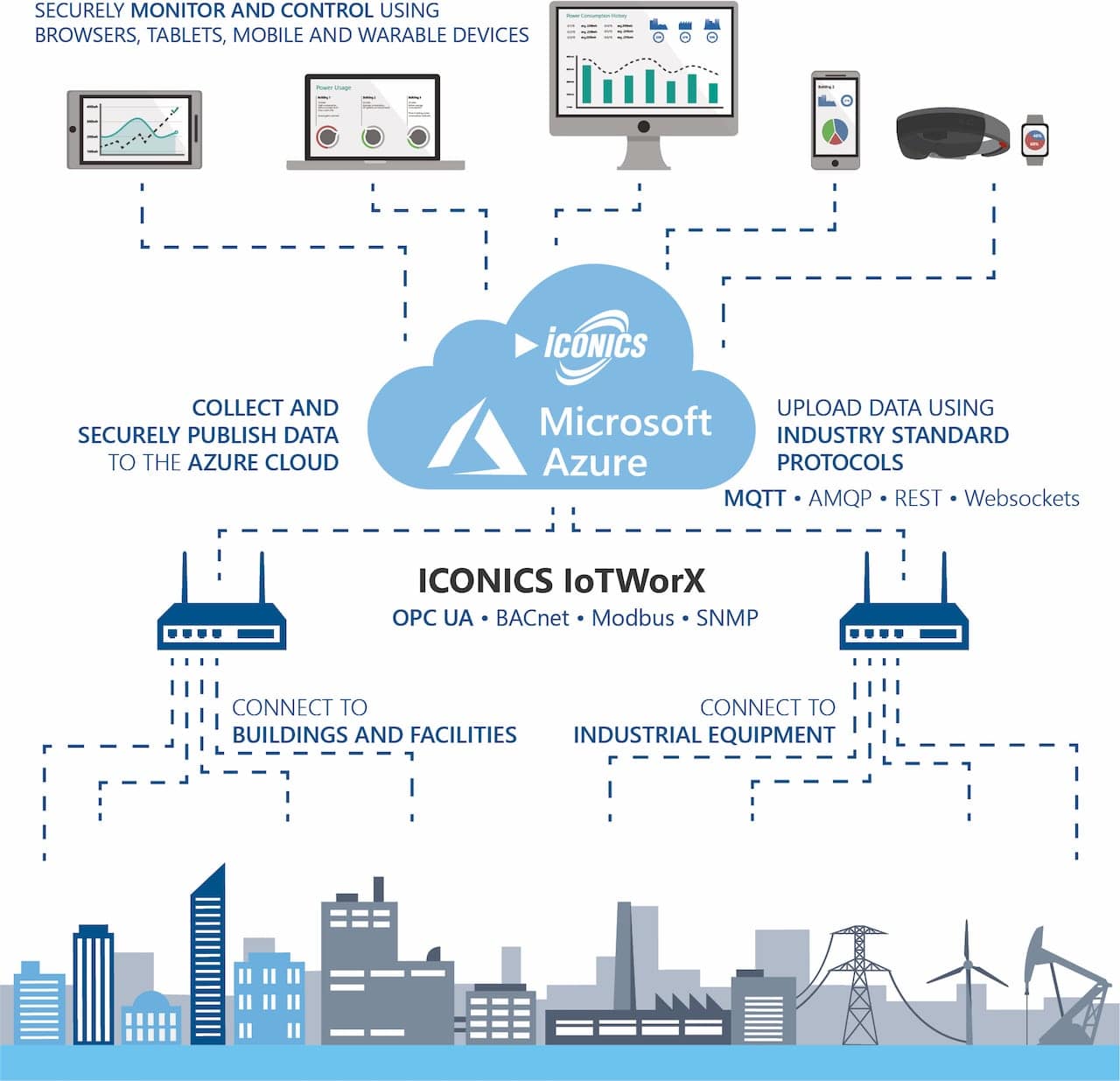
A Virtual Private Cloud (VPC) represents a virtualized network environment that allows organizations to deploy and manage resources securely within a cloud infrastructure. In the context of IoT, establishing secure connections for remote IoT VPCs is vital for ensuring seamless communication between devices and the cloud without compromising security.
IoT devices generate vast amounts of data that require secure transmission, processing, and storage. A well-structured VPC architecture provides isolation, segmentation, and control over network traffic, making it an essential component of any IoT deployment. By leveraging VPCs, organizations can create a secure and scalable environment for IoT devices, ensuring the protection of sensitive data from unauthorized access and potential cyber threats.
The Importance of Secure Connections
Securing remote IoT VPC connections is not merely about protecting data; it's about safeguarding your business and its reputation. The frequency of cyberattacks targeting IoT devices has surged in recent years, with attackers exploiting vulnerabilities in unsecured networks.
Some of the key reasons why secure connections are essential include:
- Preventing data breaches and unauthorized access to sensitive information.
- Ensuring adherence to industry standards and regulatory requirements.
- Protecting valuable intellectual property and confidential data.
- Maintaining customer trust and preserving brand reputation.
By prioritizing secure connections, organizations can significantly reduce the risk of cyber threats and ensure the smooth operation of their IoT ecosystems.
IoT VPC Architecture
Components of a Secure IoT VPC
A well-designed IoT VPC architecture incorporates several key components that work in harmony to ensure secure connections:
Read also:Naviyd Ely Raymond
- VPC Subnets: Separate network segments dedicated to different types of devices and applications, enhancing security through segmentation.
- Security Groups: Firewall rules that control inbound and outbound traffic to instances within the VPC, acting as the first line of defense.
- Network Access Control Lists (NACLs): An additional layer of security that defines allowed or denied traffic at the subnet level, providing granular control.
- Route Tables: Define how traffic is routed between subnets and external networks, ensuring efficient and secure data flow.
Design Considerations
When designing an IoT VPC architecture, it's crucial to consider factors such as scalability, redundancy, and fault tolerance. Organizations should implement network segmentation to isolate critical devices and applications from less secure ones, thereby minimizing the potential impact of a security breach.
Key Security Challenges
While VPCs offer robust security features, there are several challenges to address when securing remote IoT VPC connections:
- Device Authentication: Ensuring that only authorized devices can access the network is fundamental to maintaining security.
- Data Encryption: Protecting data in transit and at rest from interception and tampering is essential for safeguarding sensitive information.
- Network Segmentation: Preventing attackers from moving laterally within the network is critical for containing threats.
- Monitoring and Logging: Detecting and responding to suspicious activities in real-time is vital for proactive threat management.
Tackling these challenges demands a combination of advanced technical solutions, established best practices, and ongoing vigilance.
Best Practices for Secure Connections
Authentication and Authorization
Implementing robust authentication mechanisms, such as multi-factor authentication (MFA) and certificate-based authentication, is crucial for securing IoT VPC environments. Organizations should also enforce strict access controls to ensure that only authorized users and devices can access sensitive resources, thereby reducing the risk of unauthorized access.
Network Segmentation
Network segmentation involves dividing the VPC into smaller, isolated subnets to limit the potential impact of a security breach. This approach helps contain threats and prevents attackers from moving laterally within the network, enhancing overall security.
Regular Updates and Patching
Keeping all devices, applications, and infrastructure components up to date with the latest security patches is critical for mitigating vulnerabilities. Organizations should establish a structured patch management process to ensure timely updates, minimizing the risk of exploitation by cyber threats.
Technologies for Securing IoT VPC
Encryption Protocols
Utilizing encryption protocols such as TLS/SSL and IPsec can help protect data in transit between IoT devices and the VPC. These protocols ensure that sensitive information remains confidential and tamper-proof, enhancing the security of data transmission.
Firewalls and Intrusion Detection Systems
Deploying firewalls and intrusion detection systems (IDS) can significantly enhance the security of IoT VPC environments by monitoring and blocking malicious traffic. These tools provide an additional layer of defense against cyber threats, improving the overall security posture.
Cloud Security Services
Cloud providers offer a range of security services, such as AWS Shield, Azure Security Center, and Google Cloud Armor, that can help protect IoT VPC environments from distributed denial-of-service (DDoS) attacks and other threats. Leveraging these services can enhance the security of cloud-based IoT deployments.
Securing Data Transmission
Data transmission is a critical aspect of securing remote IoT VPC connections. Organizations should implement end-to-end encryption to protect data as it travels between devices, gateways, and the cloud. Using secure communication protocols such as MQTT over TLS can help ensure the integrity and confidentiality of data, safeguarding it from potential interception or tampering.
Regularly auditing and monitoring data transmission processes can help identify and address potential vulnerabilities before they are exploited by attackers, ensuring the secure flow of information within the IoT ecosystem.
Monitoring and Management
Centralized Logging and Monitoring
Implementing centralized logging and monitoring solutions can provide organizations with comprehensive visibility into their IoT VPC environments. These solutions enable real-time detection of suspicious activities and facilitate faster response times to security incidents, enhancing the overall security of the network.
Automated Incident Response
Automating incident response processes can help reduce the time and effort required to address security breaches. By leveraging tools such as Security Information and Event Management (SIEM) systems, organizations can streamline their incident response workflows, improving their ability to respond to threats effectively and efficiently.
Compliance and Regulations
When securing remote IoT VPC connections, organizations must also consider compliance with relevant regulations and standards, such as:
- GDPR: General Data Protection Regulation
- HIPAA: Health Insurance Portability and Accountability Act
- ISO 27001: Information Security Management System
Adhering to these regulations ensures that organizations meet legal requirements and protect sensitive data, maintaining trust with customers and stakeholders.
Future Trends in IoT Security
As IoT technology continues to evolve, so too will the methods for securing remote IoT VPC connections. Some emerging trends in IoT security include:
- Artificial Intelligence (AI) and Machine Learning (ML): AI and ML can enhance threat detection and response capabilities by analyzing large datasets and identifying patterns indicative of malicious activity, providing proactive protection against cyber threats.
- Zero Trust Architecture: Adopting a zero trust model can help organizations minimize the risk of insider threats and unauthorized access by continuously verifying identities and permissions, ensuring that only authorized entities can access sensitive resources.
- Quantum Cryptography: Quantum cryptography offers advanced encryption techniques that are resistant to quantum computing attacks, providing long-term security for IoT devices and ensuring the confidentiality of sensitive data.
Staying informed about these trends can help organizations stay ahead of potential threats and ensure the continued security of their IoT VPC environments.
Conclusion and Next Steps
In conclusion, securing remote IoT VPC connections is a multifaceted challenge that demands a comprehensive approach. By implementing best practices, leveraging advanced technologies, and maintaining compliance with relevant regulations, organizations can protect their IoT ecosystems and ensure the secure transmission of data.
We encourage readers to take the following steps:
- Review and update your current IoT VPC architecture to incorporate the latest security measures, ensuring alignment with evolving threats and technologies.
- Stay informed about emerging trends and technologies in IoT security to remain proactive in addressing potential vulnerabilities.
- Engage with industry experts and peers to share knowledge and best practices, fostering a collaborative approach to enhancing IoT security.
Feel free to leave a comment or share this article with others who may find it useful. For more insights into IoT security and related topics, explore our other articles on the website.