Securing and managing IoT devices remotely using SSH is a fundamental skill for anyone working with Raspberry Pi. Whether you're a beginner or an advanced user, this guide will walk you through the process of setting up SSH, connecting remotely, securing your connections, and exploring advanced features to enhance your IoT projects.
In today’s interconnected world, the Internet of Things (IoT) has transformed industries by enabling devices to communicate and share data seamlessly. As IoT adoption continues to grow, the importance of secure and efficient remote management tools becomes increasingly critical. Secure Shell (SSH) stands out as one of the most reliable protocols for controlling and managing remote devices, especially for Raspberry Pi-based IoT setups. This article will provide a comprehensive overview of SSH, its integration with Raspberry Pi, and practical tips for maximizing its potential in your IoT projects.
By the end of this guide, you will have a thorough understanding of SSH remote management for Raspberry Pi, including setup procedures, troubleshooting strategies, and best practices for maintaining security. Let’s explore how SSH can revolutionize the way you manage your IoT devices.
Read also:Irene Banerjee
Table of Contents
- Introduction to SSH and Its Importance
- Overview of Raspberry Pi in IoT Applications
- Setting Up SSH on Your Raspberry Pi
- Connecting Remotely via SSH
- Securing Your SSH Connection
- Common Issues and Troubleshooting
- Advanced SSH Features for IoT
- Downloading and Installing SSH Clients
- Best Practices for SSH Remote IoT Raspberry Pi
- Conclusion and Next Steps
The Role of SSH in Secure Remote Management
Understanding the Secure Shell Protocol
SSH, or Secure Shell, is a cryptographic network protocol designed to facilitate secure communication between devices over potentially unsecured networks. It is widely regarded as a robust solution for remote command-line login and secure data transfer. In the realm of IoT, SSH ensures that your devices remain accessible while protecting them from unauthorized access and cyber threats.
For Raspberry Pi users, SSH offers an unparalleled advantage by enabling remote management without the need for physical access. This capability is particularly valuable for IoT projects where devices are often deployed in remote or hard-to-reach locations, such as smart home systems, environmental sensors, or industrial monitoring solutions.
Why SSH is Indispensable for IoT Applications
In IoT environments, where security is paramount, SSH plays a vital role in safeguarding your devices and data. By encrypting all communications between the client and server, SSH effectively prevents unauthorized interception and tampering of sensitive information. Beyond security, SSH also provides additional functionalities such as file transfer, port forwarding, and secure tunneling, making it an indispensable tool for managing IoT devices.
These features collectively enhance the efficiency and reliability of your IoT projects, ensuring seamless operation even in challenging network conditions.
Raspberry Pi: The Ideal Platform for IoT Development
Raspberry Pi has emerged as a leading choice for both hobbyists and professionals due to its affordability, versatility, and ease of use. With its compact size, low power consumption, and compatibility with a wide range of operating systems, Raspberry Pi serves as an excellent foundation for developing IoT applications. From home automation systems to advanced industrial solutions, Raspberry Pi continues to redefine the possibilities of IoT innovation.
Key Features That Make Raspberry Pi Ideal for IoT
- Compact Design and Low Power Consumption: Perfect for deploying in constrained environments where energy efficiency is critical.
- Wide Range of Operating Systems: Supports popular operating systems like Raspberry Pi OS, Ubuntu, and others, providing flexibility for diverse applications.
- Extensive GPIO Capabilities: Equipped with General Purpose Input/Output pins, enabling seamless integration with external sensors and devices.
- Community Support and Documentation: A vibrant community of developers and enthusiasts contributes to a wealth of resources, tutorials, and support.
When combined with SSH for secure remote management, Raspberry Pi becomes an even more powerful tool for IoT projects, empowering users to manage their devices efficiently and securely.
Read also:Hdhub4uin Guru Your Ultimate Guide To Educational Resources And Beyond
Enabling SSH on Your Raspberry Pi
Step-by-Step Guide to Activating SSH
Before you can leverage SSH for remote management, you must ensure that the SSH service is enabled on your Raspberry Pi. Follow these simple steps to activate SSH:
- Power on your Raspberry Pi and connect it to a monitor and keyboard for initial setup.
- Open the terminal and enter the command
sudo raspi-configto access the configuration menu. - Navigate to "Interfacing Options" and select "SSH" to enable the service.
- Choose "Yes" when prompted to enable SSH and confirm your selection by pressing Enter.
- Reboot your Raspberry Pi to apply the changes and ensure that SSH is active.
Configuring SSH for Enhanced IoT Functionality
To optimize SSH for IoT applications, it’s essential to configure the service to meet specific security and functionality requirements. This includes setting up a static IP address to ensure consistent connectivity, disabling password authentication to enhance security, and implementing SSH keys for secure access.
By carefully configuring SSH according to these guidelines, you can ensure that your Raspberry Pi is fully prepared for secure and efficient remote management in IoT environments.
Establishing a Secure Remote Connection via SSH
Selecting and Using an SSH Client
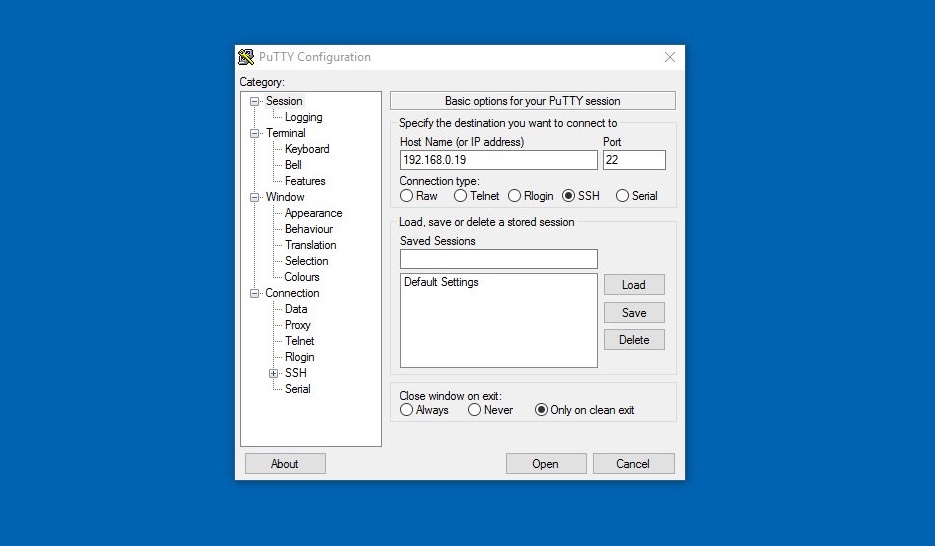
To connect to your Raspberry Pi remotely, you will need an SSH client. Depending on your operating system, there are several options available. For Windows users, popular choices include PuTTY, while macOS and Linux users can utilize the built-in SSH command-line tool. Below is an example of how to connect using the terminal:
- Open the terminal application on your computer.
- Enter the command
ssh pi@your-raspberry-pi-ip-address, replacing "your-raspberry-pi-ip-address" with the actual IP address of your Raspberry Pi. - When prompted, enter the password for the Raspberry Pi user account.
Addressing Common Connection Issues
Even with proper setup, challenges may arise when attempting to establish an SSH connection. Below are some common problems and their corresponding solutions:
- Connection Refused: Verify that the SSH service is running on your Raspberry Pi and check your network settings to ensure proper connectivity.
- Authentication Failed: Carefully review your username, password, or SSH key configuration to identify any discrepancies.
- Timeout Errors: Confirm that your Raspberry Pi is connected to the network and accessible from your client machine, and ensure that no firewalls are blocking SSH traffic.
Strengthening Your SSH Security
Implementing SSH Keys for Enhanced Protection
Using SSH keys instead of traditional passwords adds an extra layer of security to your remote connections. Follow these steps to set up SSH keys:
- Generate an SSH key pair on your local machine by running the command
ssh-keygen. - Copy the public key to your Raspberry Pi using the command
ssh-copy-id pi@your-raspberry-pi-ip-address. - Disable password authentication in the SSH configuration file to enforce key-based authentication exclusively.
Performing Regular Security Audits
To maintain a secure SSH setup, it’s crucial to conduct regular audits and updates. This involves keeping your software up to date, monitoring system logs for suspicious activity, and reviewing access permissions to ensure that only authorized users have access to your Raspberry Pi.
Resolving Common SSH Issues in IoT Applications
Despite thorough preparation, challenges may still arise when using SSH for IoT projects. Below are some frequently encountered problems and their solutions:
- Connection Refused: Ensure that the SSH service is active on your Raspberry Pi and double-check your network settings for accuracy.
- Authentication Failed: Revisit your username, password, or SSH key configuration to resolve any inconsistencies.
- Timeout Errors: Confirm that your Raspberry Pi is connected to the network and accessible from your client machine, and verify that no firewalls are obstructing SSH traffic.
Exploring Advanced SSH Features for IoT
Utilizing SSH Tunneling for Secure Data Transmission
SSH tunneling enables you to securely forward traffic between your local machine and a remote server, making it particularly useful for accessing IoT devices located behind firewalls or NATs. By setting up SSH tunnels, you can ensure that sensitive data remains protected during transmission, enhancing the overall security of your IoT setup.
Automating Routine Tasks with SSH Scripts
SSH scripts provide a powerful way to automate repetitive tasks such as data collection, system updates, and backups. By scripting these processes, you can minimize manual intervention and streamline the management of your IoT devices, ultimately increasing efficiency and reducing the risk of human error.
Selecting and Installing SSH Clients
Depending on your operating system, you may need to download and install an SSH client to facilitate remote connections. Below are some recommendations:
- Windows: Use PuTTY or leverage the Windows Subsystem for Linux (WSL) for a seamless SSH experience.
- macOS/Linux: Take advantage of the built-in SSH command-line tool for convenient and reliable connectivity.
Always ensure that you download SSH clients from reputable sources to mitigate any potential security risks.
Essential Best Practices for SSH Remote IoT Raspberry Pi Management
Staying Updated and Backing Up Your System
Keeping your Raspberry Pi’s operating system and software up to date is critical for maintaining security and optimizing performance. Additionally, implementing a regular backup routine ensures that you can quickly recover your device in the event of hardware failure or data loss.
Implementing Robust Monitoring and Logging Solutions
Establishing comprehensive monitoring and logging mechanisms allows you to stay informed about the status of your IoT devices and promptly address any emerging issues. By analyzing logs for unusual patterns or activities, you can proactively identify and resolve potential problems before they escalate into more significant challenges.
Conclusion: Elevating Your IoT Projects with SSH
In conclusion, mastering SSH remote management for IoT Raspberry Pi projects is an essential skill for anyone involved in IoT development. By following the guidance provided in this article, you can securely manage your Raspberry Pi devices from anywhere in the world, unlocking new possibilities for innovation and efficiency in your IoT endeavors.
We encourage you to further explore the capabilities of SSH by experimenting with advanced features and integrating them into your IoT projects. Share your experiences and insights in the comments below, and don’t hesitate to explore our other resources for more informative content on IoT and Raspberry Pi.
References: