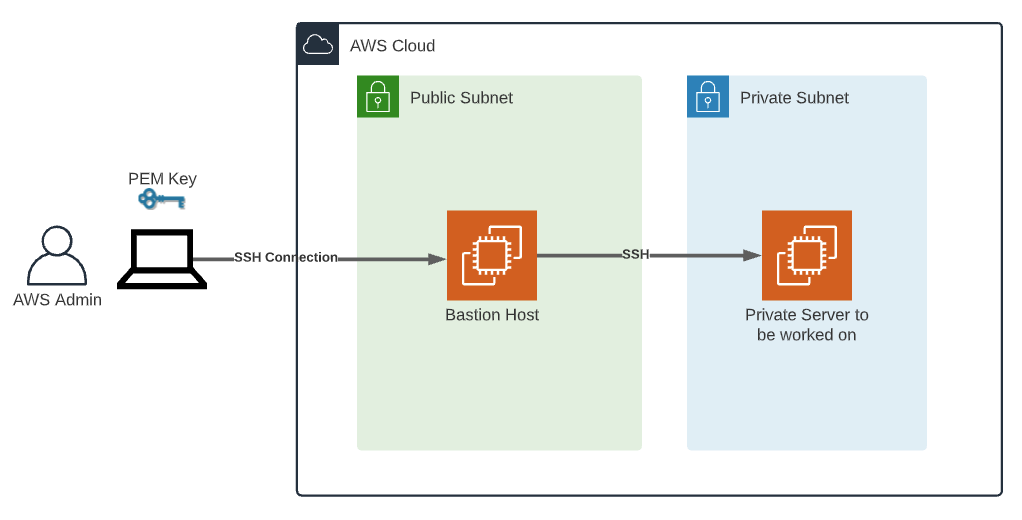
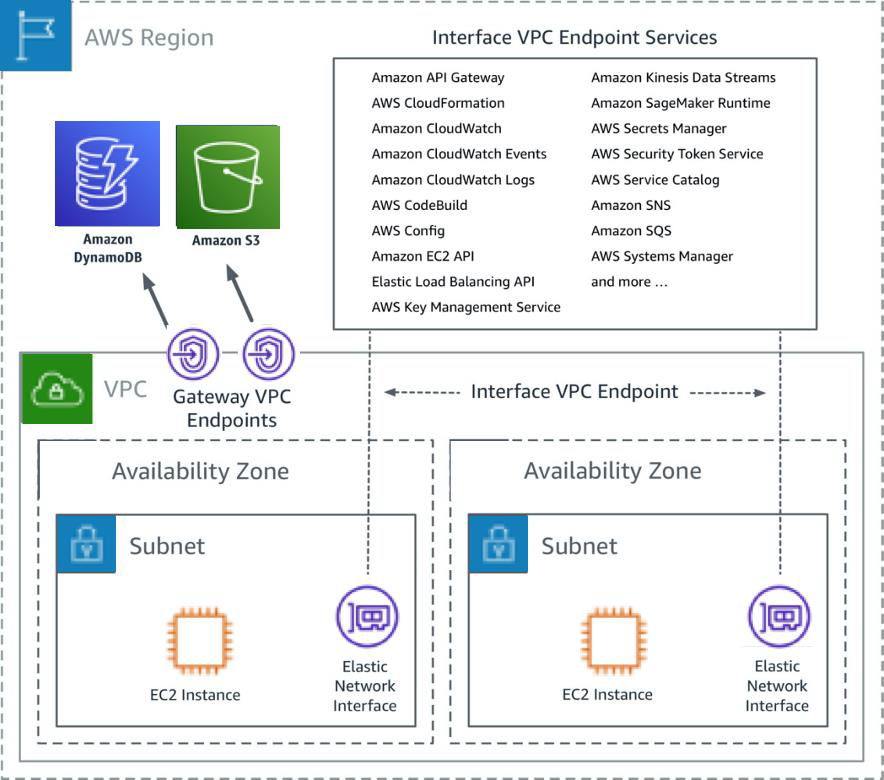
Securing cloud infrastructure through RemoteIoT VPC SSH AWS has become a top priority for businesses. As more organizations adopt cloud technologies, understanding how to configure and manage Virtual Private Cloud (VPC) with Secure Shell (SSH) on Amazon Web Services (AWS) is crucial. This guide will delve deep into the topic, equipping you with the knowledge and tools to implement secure remote IoT configurations effectively.
In today's rapidly evolving digital landscape, cloud computing has transformed the way businesses operate. AWS, as a leading provider of cloud services, offers robust solutions for secure networking, including VPC and SSH. These technologies are instrumental in safeguarding IoT devices and ensuring secure communication between remote systems, making them indispensable for modern enterprises.
This article will explore the fundamentals of RemoteIoT VPC SSH AWS in detail. From step-by-step configuration processes to advanced strategies for securing your cloud environment, this guide is designed to cater to both beginners and seasoned IT professionals. By the end, you'll have a clear understanding of how to optimize your cloud infrastructure for security and efficiency.
Read also:Understanding The Concept Of Masa 49 And Its Cultural Significance
Table of Contents
- Introduction to VPC
- Understanding SSH
- Integrating RemoteIoT with VPC on AWS
- Configuring VPC for RemoteIoT
- Setting Up SSH on AWS
- Securing RemoteIoT VPC SSH AWS
- Best Practices for RemoteIoT VPC SSH AWS
- Troubleshooting Common Issues
- Case Studies
- Conclusion
What is VPC and Why Does It Matter?
A Virtual Private Cloud (VPC) is a cornerstone of AWS that enables users to create a private, isolated section within the AWS cloud. This isolated environment grants complete control over your virtual networking setup, allowing you to define your own IP address range, create subnets, and configure route tables and network gateways. For organizations utilizing RemoteIoT applications, VPC is essential for ensuring secure communication between IoT devices and cloud resources.
VPC empowers businesses to establish precise access policies and network configurations that align with their specific needs. By leveraging VPC, companies can enhance security, optimize performance, and streamline the management of their cloud resources.
Key Features of VPC
- Customizable IP address ranges to suit your organization's requirements.
- Ability to create public and private subnets for enhanced segmentation and security.
- Support for multiple availability zones to improve reliability and fault tolerance.
- Flexible routing and network access control to manage traffic efficiently.
The Role of SSH in Secure Communication
Secure Shell (SSH) is a cryptographic network protocol designed to provide secure communication between devices and servers. It ensures strong authentication and encrypted data transmission, making it an ideal solution for managing cloud resources and IoT devices. When integrated with AWS, SSH allows administrators to securely access EC2 instances within a VPC, protecting sensitive information from unauthorized access and eavesdropping.
SSH plays a critical role in securing cloud environments, offering several advantages that make it indispensable for modern IT infrastructure. By encrypting all data transmitted between devices, SSH ensures that even if intercepted, the data remains unintelligible to unauthorized parties.
Benefits of Using SSH
- Data encryption during transmission to protect sensitive information.
- Strong authentication mechanisms to verify the identity of users and devices.
- Protection against man-in-the-middle attacks through secure connections.
- Compatibility with various operating systems, ensuring seamless integration across platforms.
Integrating RemoteIoT with VPC on AWS
Integrating RemoteIoT with VPC on AWS requires meticulous planning and configuration. Combining the capabilities of IoT devices with the scalability and security of AWS enables businesses to build robust and secure cloud-based solutions. To achieve seamless integration, it is crucial to configure VPC settings, set up SSH access, and implement security best practices. This ensures that IoT devices can communicate securely with cloud resources while maintaining high levels of performance and reliability.
By integrating RemoteIoT with VPC on AWS, organizations can leverage the full potential of IoT technologies while safeguarding their cloud infrastructure. This combination provides a foundation for building innovative solutions that drive business growth and efficiency.
Read also:Brian Musso Net Worth
Steps for Integration
- Create a VPC with appropriate subnets and routing tables to establish a secure network environment.
- Launch EC2 instances within the VPC to host your IoT applications and services.
- Configure SSH access for the instances to enable secure remote management and monitoring.
- Set up security groups and network access control lists (ACLs) to define precise access policies.
Configuring VPC for RemoteIoT Applications
Configuring VPC for RemoteIoT applications involves several critical steps, including defining the VPC's IP address range, creating subnets, and setting up routing tables and internet gateways. Proper configuration ensures that IoT devices can communicate effectively with cloud resources while maintaining a high level of security. When configuring VPC, it is essential to consider factors such as availability zones, network latency, and security requirements to optimize performance and reduce costs.
By tailoring VPC settings to your specific needs, you can create a network environment that supports the unique demands of your IoT applications. This includes ensuring low-latency connections, implementing robust security measures, and providing scalability to accommodate future growth.
Best Practices for VPC Configuration
- Use separate subnets for public and private resources to enhance security and simplify management.
- Implement network ACLs to provide an additional layer of security and control over inbound and outbound traffic.
- Monitor VPC flow logs to detect and respond to suspicious activity promptly.
- Regularly review and update security group rules to ensure they align with your evolving security needs.
Setting Up SSH on AWS for Secure Access
Setting up SSH on AWS involves creating key pairs, configuring security groups, and establishing SSH connections to EC2 instances. This process ensures that administrators can securely access cloud resources while maintaining compliance with security standards. When setting up SSH, it is important to follow best practices, such as using strong key pairs, limiting access to specific IP addresses, and regularly rotating keys. These measures help protect against unauthorized access and ensure the integrity of your cloud environment.
By implementing SSH on AWS, organizations can achieve secure and efficient management of their cloud resources. This includes enabling remote access for administrators, automating routine tasks, and monitoring system performance in real time.
Steps for Setting Up SSH
- Create a key pair in the AWS Management Console to establish secure authentication for SSH connections.
- Configure security groups to allow SSH access from trusted IP addresses, minimizing the risk of unauthorized access.
- Connect to EC2 instances using an SSH client, ensuring that all communications are encrypted and secure.
- Test the connection and verify access to ensure that SSH is configured correctly and functioning as intended.
Enhancing Security for RemoteIoT VPC SSH AWS
Securing RemoteIoT VPC SSH AWS is paramount for protecting sensitive data and ensuring the integrity of your cloud infrastructure. This involves implementing robust security measures, such as encryption, access controls, and continuous monitoring. To enhance security, consider leveraging AWS Identity and Access Management (IAM) to manage user permissions and roles effectively. Additionally, regularly review and update security policies to address emerging threats and vulnerabilities.
By prioritizing security, organizations can safeguard their cloud infrastructure against potential threats and ensure the seamless operation of their IoT applications. This includes implementing encryption for data at rest and in transit, enabling multi-factor authentication (MFA) for added security, and deploying intrusion detection and prevention systems (IDPS) to monitor for suspicious activity.
Security Measures for RemoteIoT VPC SSH AWS
- Enable encryption for all data stored and transmitted to protect against unauthorized access.
- Use multi-factor authentication (MFA) to strengthen user authentication and reduce the risk of unauthorized access.
- Implement intrusion detection and prevention systems (IDPS) to identify and respond to potential threats in real time.
- Regularly audit security configurations and logs to identify and address vulnerabilities proactively.
Best Practices for Optimizing RemoteIoT VPC SSH AWS
Following best practices for RemoteIoT VPC SSH AWS can significantly improve the security and performance of your cloud infrastructure. These practices include proper configuration, regular maintenance, and continuous monitoring. By adhering to best practices, businesses can minimize risks, optimize resource utilization, and ensure compliance with industry standards and regulations.
Implementing best practices not only enhances security but also improves the overall efficiency of your cloud infrastructure. This includes regularly updating software and security patches, limiting access to critical resources using IAM roles, and implementing network segmentation for enhanced security. Additionally, monitoring resource usage and adjusting configurations as needed ensures that your infrastructure remains optimized for performance and scalability.
Key Best Practices
- Regularly update software and security patches to address known vulnerabilities and improve system reliability.
- Limit access to critical resources using IAM roles to ensure that only authorized users can perform sensitive operations.
- Implement network segmentation to isolate sensitive resources and reduce the attack surface of your cloud infrastructure.
- Monitor resource usage and adjust configurations dynamically to optimize performance and reduce costs.
Troubleshooting Common Issues in RemoteIoT VPC SSH AWS
Even with careful planning and configuration, challenges may arise when working with RemoteIoT VPC SSH AWS. Common issues include connectivity problems, permission errors, and configuration mismatches. To troubleshoot these issues effectively, start by reviewing logs and error messages for clues. Additionally, consult AWS documentation and support resources for guidance on resolving specific problems.
By addressing issues promptly and systematically, organizations can minimize downtime and ensure the smooth operation of their cloud infrastructure. This includes verifying security group rules and network ACLs, testing connectivity using tools like ping and traceroute, and reviewing VPC flow logs for detailed insights into network activity.
Troubleshooting Tips
- Check security group rules and network ACLs to ensure they align with your intended access policies.
- Verify key pair settings and permissions to confirm that SSH connections are configured correctly.
- Test connectivity using tools like ping and traceroute to identify and resolve network-related issues.
- Review VPC flow logs for detailed insights into network traffic and potential issues.
Real-World Examples of RemoteIoT VPC SSH AWS Implementations
Examining real-world case studies of RemoteIoT VPC SSH AWS implementations provides valuable insights into the benefits and challenges of integrating these technologies. For instance, a manufacturing company successfully implemented RemoteIoT VPC SSH AWS to securely monitor and manage their IoT devices. By leveraging VPC and SSH, they achieved improved performance, enhanced security, and reduced operational costs.
These case studies highlight the importance of proper planning, configuration, and security measures in achieving successful RemoteIoT VPC SSH AWS implementations. They also emphasize the need for continuous monitoring and optimization to address evolving challenges and opportunities.
Conclusion: Unlocking the Potential of RemoteIoT VPC SSH AWS
Mastering RemoteIoT VPC SSH AWS is essential for businesses seeking to secure their cloud infrastructure while enabling seamless remote access. This guide has provided a comprehensive overview of the subject, covering key concepts, configuration steps, and best practices. By following the recommendations outlined in this guide, organizations can build robust, secure, and efficient cloud-based solutions that drive innovation and growth.
To further enhance your understanding and implementation, consider exploring additional AWS resources and documentation. Additionally, don't hesitate to reach out to AWS support for assistance with specific issues or questions. Your feedback and experiences are invaluable in helping us improve and provide valuable insights for the community.
We invite you to share your thoughts and experiences in the comments section below. Your contributions help us refine our content and offer meaningful guidance to others. For more informative articles and guides, explore our website and stay updated on the latest trends in cloud computing and IoT.