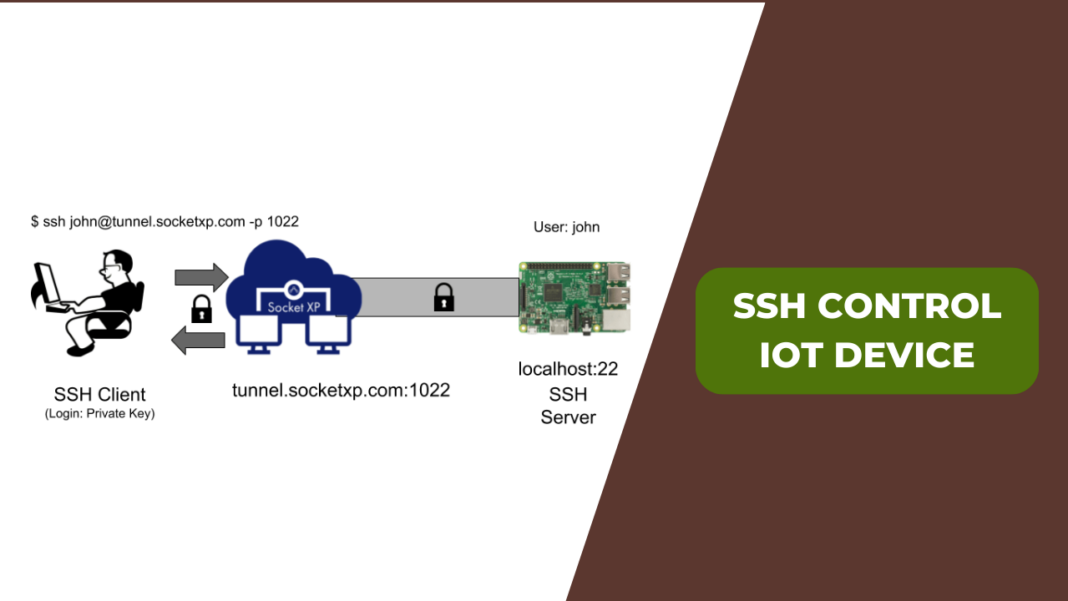
Secure remote management of IoT devices using SSH has become a critical component of modern technology. As IoT adoption grows across industries, understanding how to manage these devices effectively and securely is more important than ever. Whether you're a seasoned network administrator, a developer, or a tech enthusiast, this guide will equip you with the tools and knowledge to manage your IoT infrastructure efficiently using SSH.
In today’s interconnected world, the ability to access and manage IoT devices remotely via SSH offers unparalleled convenience and efficiency. From smart home systems to industrial sensors, SSH provides a secure and reliable way to interact with these devices without requiring physical presence. However, with this power comes the responsibility to ensure the security and integrity of your SSH connections, which is essential in safeguarding your IoT ecosystem.
This comprehensive article dives deep into the world of SSH remote IoT device management. It covers everything from the basics of SSH to advanced techniques for securing your connections. Whether you're a beginner or looking to refine your existing knowledge, this guide will provide you with the insights and best practices needed to excel in IoT device management.
Read also:Hdhub4uin Guru Your Ultimate Guide To Educational Resources And Beyond
Table of Contents
- Understanding SSH
- The Role of SSH in IoT Device Management
- Setting Up Basic SSH Access
- Advanced SSH Configuration
- Best Practices for SSH Security
- Troubleshooting Common SSH Issues
- Using SSH Keys for Enhanced Authentication
- Optimizing SSH Performance for IoT Devices
- Leveraging Automation Scripts for Efficient SSH Management
- Emerging Trends in SSH IoT Device Management
- Conclusion
Understanding SSH
Secure Shell (SSH) is a cryptographic network protocol that facilitates secure communication between devices over potentially insecure networks. First developed in 1995, SSH has evolved into an indispensable tool for system administrators and developers. Its primary function is to provide a secure channel for remote access and file transfer, making it essential for managing IoT devices remotely.
What Sets SSH Apart?
SSH distinguishes itself through its robust encryption and authentication mechanisms. Unlike other protocols, SSH ensures data integrity and confidentiality by encrypting all transmitted information. This makes it an ideal solution for IoT device management, where sensitive data is frequently involved. Additionally, SSH supports various authentication methods, including password-based and public key authentication, offering flexibility and enhanced security.
The Role of SSH in IoT Device Management
In the rapidly expanding field of IoT, SSH plays a pivotal role in ensuring secure and efficient device management. With IoT devices often deployed in remote locations, having a reliable method for remote access is essential. SSH not only provides this capability but also maintains a high level of security, protecting both the devices and the data they handle.
Key Advantages of Using SSH for IoT Devices
- Enhanced Security: SSH encrypts all communication, preventing unauthorized access and safeguarding against data breaches.
- Remote Accessibility: Administrators can manage IoT devices from anywhere, streamlining operations and minimizing downtime.
- Scalability: SSH is capable of handling large-scale IoT deployments, ensuring consistent performance across numerous devices.
Setting Up Basic SSH Access
Getting started with SSH is relatively simple. Most modern operating systems, including Linux, macOS, and Windows, come with built-in SSH clients. Below is a step-by-step guide to setting up basic SSH access for your IoT devices:
Steps to Configure SSH
- Ensure SSH is installed on your IoT device. Many Linux-based devices come with SSH pre-installed.
- Enable the SSH service by running the command
sudo systemctl enable ssh. - Start the SSH service using
sudo systemctl start ssh. - Test the connection by running
ssh username@device_ipfrom your local machine.
Advanced SSH Configuration
While basic SSH setup suffices for many use cases, advanced configuration can significantly enhance security and performance. Below are some advanced SSH settings to consider:
Tips for Advanced SSH Configuration
- Disable Password Authentication: Use public key authentication to eliminate the risk of brute-force attacks.
- Change Default Port: Switch from the default port 22 to a custom port to reduce unauthorized access attempts.
- Implement Firewall Rules: Restrict SSH access to specific IP addresses or ranges for added security.
Best Practices for SSH Security
Security should always be a top priority when managing IoT devices remotely via SSH. Below are some best practices to ensure the safety of your SSH connections:
Read also:Naviyd Ely Raymond
Essential Security Measures
- Regularly Update SSH Software: Keep your SSH client and server software up to date to address vulnerabilities.
- Limit User Access: Grant SSH access only to trusted users and restrict privileges wherever possible.
- Monitor Logs: Regularly review SSH logs for suspicious activity and take immediate action if necessary.
Troubleshooting Common SSH Issues
Even with proper configuration, SSH issues can arise. Below are some common problems and their solutions:
Common SSH Problems and Solutions
- Connection Refused: Ensure the SSH service is running and the correct port is being used.
- Authentication Failure: Verify the accuracy of your username, password, or key file.
- Timeout Errors: Check network connectivity and firewall settings to resolve these issues.
Using SSH Keys for Enhanced Authentication
SSH keys provide a more secure alternative to password-based authentication. By generating a public-private key pair, you can authenticate without entering a password, reducing the risk of unauthorized access.
How to Generate SSH Keys
- Run the command
ssh-keygento generate a key pair. - Copy the public key to the IoT device using
ssh-copy-id username@device_ip. - Test the connection to ensure key-based authentication works.
Optimizing SSH Performance for IoT Devices
Optimizing SSH performance is crucial for efficient IoT device management. Below are some strategies to improve SSH performance:
Performance Optimization Techniques
- Use Compression: Enable SSH compression to reduce data transfer times.
- Limit Ciphers: Use faster encryption algorithms to speed up connections.
- Implement Keepalive: Prevent disconnections due to inactivity by enabling keepalive settings.
Leveraging Automation Scripts for Efficient SSH Management
Automation scripts can significantly streamline SSH management tasks. By scripting repetitive processes, you can save time and reduce the likelihood of human error.
Sample SSH Automation Script
Below is an example of a simple bash script for automating SSH commands:
#!/bin/bash ssh user@device_ip "sudo systemctl restart service_name"
Emerging Trends in SSH IoT Device Management
As technology continues to evolve, so too will the methods for managing IoT devices remotely via SSH. Emerging trends include:
Upcoming Developments
- Quantum-Resistant Encryption: New encryption methods to withstand quantum computing threats.
- AI-Driven Security: Artificial intelligence for real-time threat detection and response.
- Enhanced Automation: More sophisticated automation tools to simplify device management.
Conclusion
In summary, SSH remote IoT device management is a critical skill for anyone involved in IoT technology. By following the guidelines and best practices outlined in this article, you can ensure secure and efficient management of your IoT devices. It’s important to regularly update your knowledge and skills to keep pace with the rapidly evolving world of IoT and cybersecurity.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, explore other articles on our site for more insights into IoT and related technologies. Together, we can build a safer and more connected future.