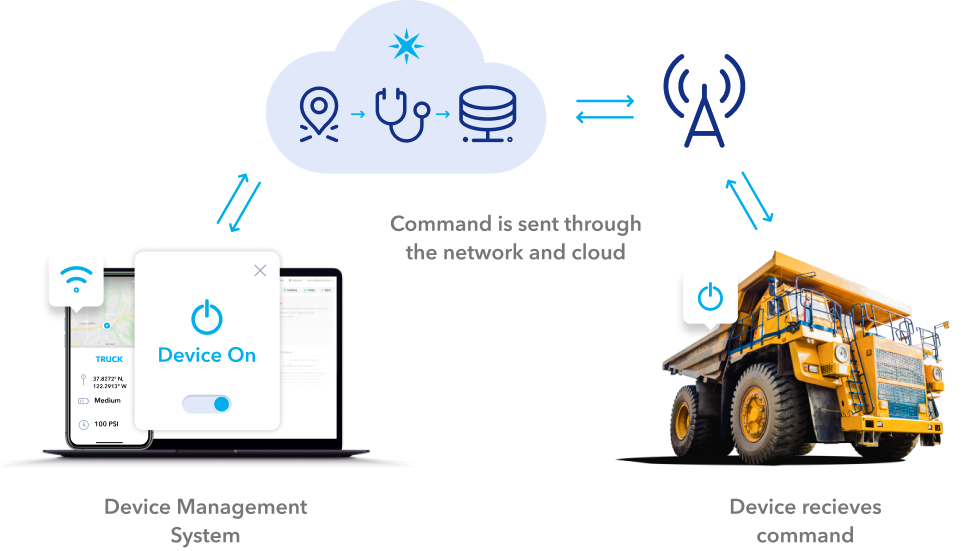
In today's highly connected world, the ability to remotely manage and monitor IoT devices has become an indispensable feature for both businesses and individuals. Remote login offers unmatched convenience and efficiency, allowing users to control their devices from anywhere. However, ensuring the security and cost-effectiveness of this process is vital to maintaining the integrity of your IoT infrastructure. In this article, we delve into the concept of remote login for IoT devices, offering practical solutions for free implementation and emphasizing the security considerations you should prioritize.
In an era where more devices are joining the Internet of Things (IoT), the demand for robust remote access solutions continues to grow exponentially. Whether you're managing smart home systems or overseeing industrial automation, remote login capabilities empower users to control, configure, and troubleshoot devices from any location across the globe. While numerous paid services exist, it is entirely feasible to establish a secure remote login system for IoT devices without incurring any costs.
This comprehensive guide will walk you through setting up remote login for IoT devices at no cost, addressing critical aspects such as security, scalability, and usability. Whether you're a tech enthusiast eager to expand your knowledge or a professional aiming to enhance your IoT infrastructure, this article will equip you with valuable insights and actionable advice.
Read also:Does Jonny Lee Miller Have Tattoos
Table of Contents
- Understanding Remote Login for IoT Devices
- Advantages of Remote Login for IoT Devices
- Critical Security Considerations for Remote Login
- Free Methods to Enable Remote Login
- Essential Tools and Software for Remote Access
- Comprehensive Step-by-Step Setup Guide
- Solving Common Remote Login Issues
- Ensuring Scalability for Future Growth
- Best Practices for Secure Remote Login
- The Evolution of IoT Remote Login
- Conclusion and Next Steps
Understanding Remote Login for IoT Devices
Remote login for IoT devices refers to the ability to access and control internet-connected devices from a distant location. This functionality plays a pivotal role in managing smart home appliances, monitoring industrial machinery, or administering networked devices across various industries. As the adoption of IoT devices continues to rise, remote access has transitioned from being a luxury to a necessity.
Despite its significance, implementing secure remote login can pose challenges. Many users opt for paid services that provide robust security features, but these often come with substantial costs. Fortunately, there are cost-effective alternatives that allow you to set up remote login for IoT devices without compromising on security or functionality.
Why Remote Login is Essential
Remote login empowers users to perform a variety of tasks seamlessly, including:
- Monitoring the status and performance of devices in real-time.
- Updating firmware and software configurations effortlessly.
- Diagnosing and resolving issues without requiring physical access.
- Enhancing operational efficiency while minimizing downtime.
Advantages of Remote Login for IoT Devices
Integrating remote login into your IoT setup offers numerous benefits for both individuals and businesses. Let's explore some of the key advantages in greater detail:
Boosted Efficiency
With remote login capabilities, you can effortlessly manage multiple devices from a centralized location, saving valuable time and resources. This is especially advantageous for businesses that rely heavily on IoT devices for their day-to-day operations.
Cost Reduction
Eliminating the need for frequent site visits can drastically cut operational expenses. Moreover, leveraging free remote login solutions enables you to bypass the costly subscription fees typically associated with proprietary software.
Read also:Lola Shark Tale
Advanced Security
Modern remote login tools are equipped with cutting-edge security features, such as encryption and two-factor authentication (2FA), ensuring that your IoT devices remain safeguarded against unauthorized access.
Critical Security Considerations for Remote Login
While remote login for IoT devices offers numerous benefits, it also introduces potential security vulnerabilities. Below are some essential considerations to keep in mind:
Data Encryption
It is imperative to encrypt all data transmitted during remote login sessions using industry-standard protocols like TLS or SSL. This prevents malicious actors from intercepting or eavesdropping on sensitive information.
Authentication and Authorization
Implementing strong authentication mechanisms, such as two-factor authentication (2FA), ensures the identity of users attempting to access your IoT devices. Additionally, enforcing role-based access control (RBAC) limits privileges based on user roles, further enhancing security.
Regular Updates
Keeping your IoT devices and remote login software up to date with the latest security patches and firmware updates is crucial. This ensures that any vulnerabilities are promptly addressed, minimizing the risk of exploitation.
Free Methods to Enable Remote Login
Several free methods are available for enabling remote login for IoT devices. Below, we delve into some of the most popular options:
SSH (Secure Shell)
SSH is a widely adopted protocol for secure remote access, providing encrypted communication between devices. It supports various authentication methods, including password-based and public-key authentication, ensuring secure interactions.
Port Forwarding
Port forwarding allows you to map a specific port on your router to an IoT device on your local network. This facilitates secure external access to your IoT device over the internet, enhancing accessibility.
Dynamic DNS (DDNS)
Dynamic DNS services assign a fixed domain name to your dynamic IP address, simplifying remote access to your IoT devices. Numerous free DDNS providers offer reliable and secure solutions, making it easier to manage your devices remotely.
Essential Tools and Software for Remote Access
To streamline remote login for IoT devices, several powerful tools and software solutions are available. Below, we highlight some of the most effective options:
TeamViewer
TeamViewer is a widely recognized remote access tool that supports IoT devices. While the basic version is free for personal use, it offers robust features such as file transfer, screen sharing, and remote control, enhancing your remote access capabilities.
NGROK
NGROK is a free tunneling tool that securely exposes local servers to the internet. It is particularly useful for testing and debugging IoT applications in a remote environment, providing developers with invaluable flexibility.
OpenVPN
OpenVPN is an open-source virtual private network (VPN) solution that enables secure remote access to IoT devices. By creating a private network, it protects your devices from unauthorized access and potential data breaches.
Comprehensive Step-by-Step Setup Guide
Setting up remote login for IoT devices involves a series of steps. Below, we provide a detailed guide to help you navigate the process:
Step 1: Identify Your IoT Device
Begin by determining which IoT device you wish to enable for remote login. Note its IP address, port number, and any other pertinent details to ensure a smooth setup process.
Step 2: Configure Port Forwarding
Access your router's admin interface and configure port forwarding to direct incoming traffic to your IoT device. Verify that the required ports are open and accessible from the internet to ensure seamless connectivity.
Step 3: Set Up Dynamic DNS
Register for a free DDNS service and link it to your router. This allows you to access your IoT device using a fixed domain name, even if your IP address changes dynamically.
Step 4: Secure Your Connection
Implement encryption and authentication mechanisms to safeguard your remote login sessions. Utilize SSH or a similar protocol to establish a secure connection to your IoT device, ensuring data integrity.
Solving Common Remote Login Issues
Even with meticulous planning, issues may arise when setting up remote login for IoT devices. Below, we address some common problems and their corresponding solutions:
Connection Timeout
If you encounter connection timeouts, review your router's firewall settings and confirm that the necessary ports are open. Additionally, ensure that your IoT device is reachable from the local network to resolve connectivity issues.
Authentication Failures
Authentication issues may stem from incorrect credentials or misconfigured settings. Carefully verify your username, password, and authentication method to address and resolve these problems effectively.
Performance Issues
Slow performance during remote login sessions might result from network congestion or insufficient bandwidth. Optimize your network settings and consider upgrading your internet plan to enhance performance and reliability.
Ensuring Scalability for Future Growth
As your IoT infrastructure expands, it is crucial to ensure that your remote login solution can accommodate future growth. Below, we outline some strategies for maintaining scalability:
Utilize a Centralized Management Platform
Implementing a centralized platform to manage all your IoT devices and remote login sessions simplifies administration and reduces the likelihood of errors. This streamlined approach ensures efficient management as your infrastructure grows.
Automate Routine Tasks
Automating repetitive tasks such as firmware updates and configuration changes saves time and enhances efficiency. Leverage scripting languages or automation tools to optimize your workflow and minimize manual intervention.
Monitor Performance Metrics
Regularly tracking performance metrics like latency, bandwidth usage, and session duration helps identify potential bottlenecks. Use this data to refine and optimize your remote login setup, ensuring consistent performance.
Best Practices for Secure Remote Login
To ensure the security and reliability of your remote login setup, adhere to the following best practices:
Create Strong Passwords
Develop strong, complex passwords for all your IoT devices and remote login accounts. Avoid using default credentials and update your passwords regularly to maintain security.
Restrict Access
Limit access to your IoT devices to authorized users only. Employ IP whitelisting or other access control mechanisms to prevent unauthorized access and enhance security.
Audit Logs Regularly
Monitor access logs for suspicious activity and promptly investigate any anomalies. This proactive approach helps detect and mitigate potential security threats before they escalate.
The Evolution of IoT Remote Login
As the IoT ecosystem continues to evolve, remote login solutions are expected to become increasingly advanced. Emerging technologies such as blockchain, artificial intelligence, and edge computing will significantly influence the future of IoT remote login.
Blockchain for Enhanced Security
Blockchain technology offers a decentralized and tamper-proof method for securing IoT devices. By integrating blockchain, remote login sessions can achieve higher levels of security and transparency, safeguarding against potential threats.
AI-Driven Automation
Artificial intelligence can automate numerous aspects of remote login, from threat detection to configuration management. This reduces the administrative burden and improves overall efficiency, paving the way for smarter and more efficient IoT ecosystems.
Conclusion and Next Steps
Remote login for IoT devices is a transformative tool that enhances convenience, efficiency, and security. By following the steps outlined in this article, you can establish a secure and cost-effective remote login system for your IoT devices. Always prioritize security and scalability as your IoT infrastructure expands to ensure long-term success.
We invite you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our website for further insights into IoT and related technologies. Together, let's build a smarter, safer, and more connected world!
Sources: