Establishing secure connections for remote IoT devices using P2P SSH on a Raspberry Pi has become a vital skill for both hobbyists and professionals. As the Internet of Things (IoT) continues to expand, ensuring secure communication between devices is no longer optional but a fundamental requirement. This comprehensive guide explores the process of setting up a secure SSH connection on a Raspberry Pi, enabling you to manage and access your IoT devices remotely with confidence.
In today's highly interconnected world, IoT devices are reshaping the way we live and work. However, with this advancement comes the critical responsibility of safeguarding these devices against potential cyber threats. By implementing P2P SSH, users can create encrypted communication channels, protecting sensitive data and ensuring privacy. This guide provides a detailed, step-by-step approach to help you securely connect IoT devices using a Raspberry Pi, catering to beginners and advanced users alike.
Table of Contents
- Introduction to Secure IoT Connections
- Raspberry Pi: An Overview
- Understanding SSH Basics
- Peer-to-Peer SSH Connections
- Steps to Securely Connect IoT Devices
- Enabling Remote Access
- Essential Tools for Download and Setup
- Best Practices for Security
- Troubleshooting Common Issues
- Conclusion and Next Steps
Introduction to Secure IoT Connections
IoT devices have revolutionized industries by enabling smart homes, connected cars, and industrial automation. However, without proper security measures, these devices can become vulnerable to attacks. Establishing secure connections for remote IoT devices through P2P SSH on a Raspberry Pi is essential to maintaining data integrity and privacy. This process not only protects sensitive information but also enhances the reliability of IoT networks.
Read also:Will Ferrel Teeth
Why Security Matters in IoT
In the realm of IoT, security breaches can have severe consequences, ranging from unauthorized access to data theft and even physical damage. For example, a compromised smart home device could allow hackers to access personal information or gain control over home systems remotely. Ensuring robust security measures is crucial to protect both individuals and organizations from potential threats.
Role of Raspberry Pi in IoT
Raspberry Pi serves as an affordable and versatile platform for building IoT projects. Its compact design, low power consumption,, and compatibility with various sensors make it an ideal choice for IoT applications. With its user-friendly interface and extensive community support, Raspberry Pi has become a popular choice for both beginners and experienced developers.
Raspberry Pi: An Overview
Raspberry Pi is a single-board computer developed by the Raspberry Pi Foundation. It is widely used in educational settings and by hobbyists for a variety of projects, from media centers to robotics. Its affordability and flexibility have made it a staple in the tech community.
Key Features of Raspberry Pi
- Compact and lightweight design, making it easy to integrate into various projects
- Support for multiple operating systems, providing flexibility for different use cases
- GPIO pins for connecting external devices, enabling interaction with the physical world
- Built-in Wi-Fi and Bluetooth capabilities, facilitating wireless connectivity
Understanding SSH Basics
SSH (Secure Shell) is a cryptographic network protocol designed for secure communication over unsecured networks. It provides a secure channel for remote command execution and file transfer, ensuring that data transmitted between devices remains protected from unauthorized access.
How SSH Works
SSH employs encryption to safeguard data in transit, ensuring that even if intercepted, the information remains unreadable to unauthorized parties. It supports various authentication methods, including passwords and public-key cryptography, allowing users to choose the most secure option for their specific needs.
Peer-to-Peer SSH Connections
Peer-to-peer (P2P) SSH connections enable devices to communicate directly without relying on centralized servers. This approach offers several advantages, including reduced latency, improved data privacy, and enhanced security by minimizing intermediate points of failure. By eliminating the need for third-party servers, P2P SSH ensures a more direct and secure communication channel.
Read also:Peter Stormare In Prison Break
Advantages of P2P SSH
- Decreased reliance on third-party servers, reducing potential security risks
- Enhanced data privacy through direct communication between devices
- Lower latency and faster communication, improving overall performance
Steps to Securely Connect IoT Devices
Securing remote IoT devices using P2P SSH on a Raspberry Pi involves several critical steps. By following these instructions, you can establish a robust and secure connection for your IoT projects:
Step 1: Set Up Raspberry Pi
Begin by installing the latest version of Raspberry Pi OS on your device. Ensure that all updates and security patches are applied to maintain the highest level of protection. A well-configured Raspberry Pi serves as the foundation for a secure IoT network.
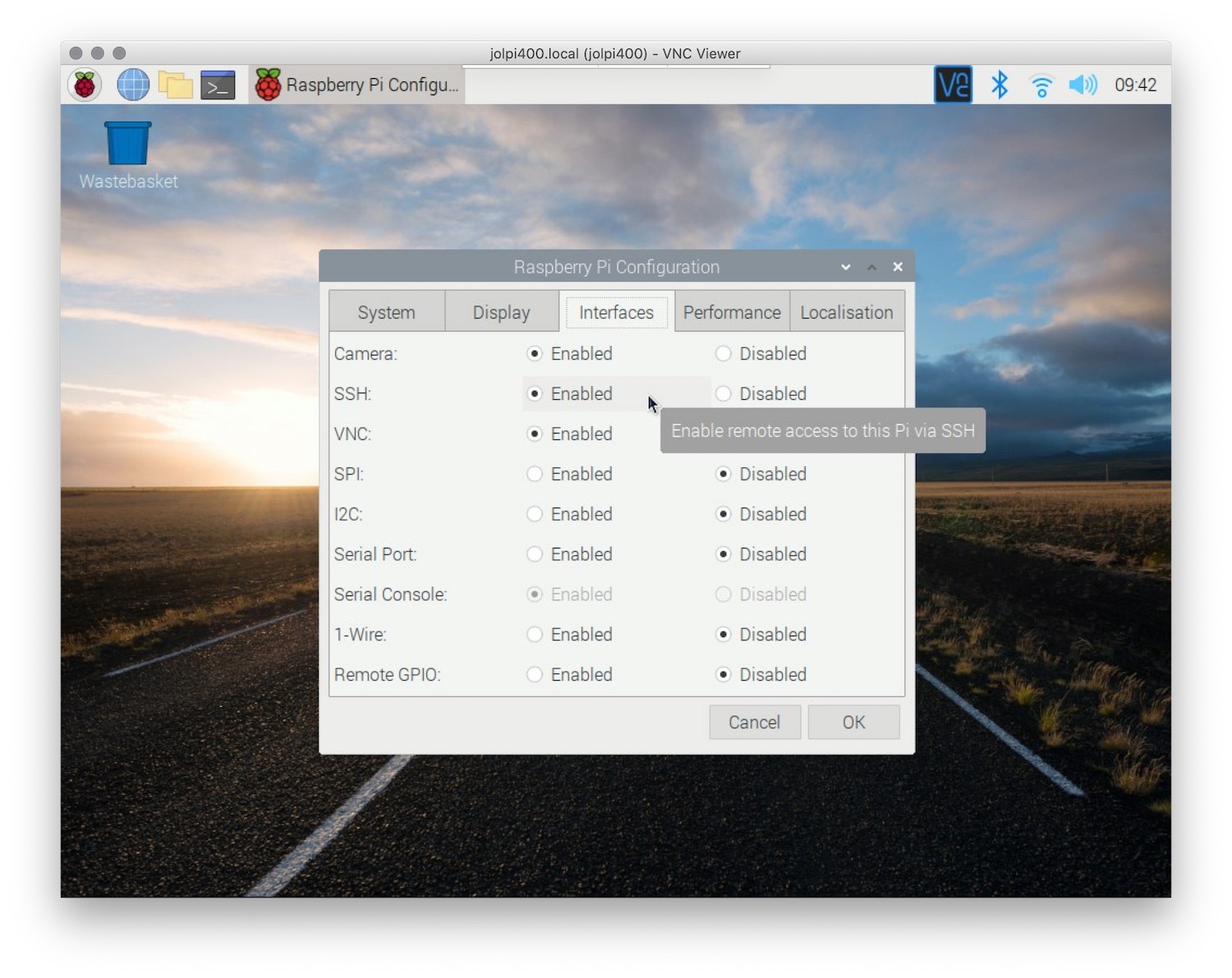
Step 2: Enable SSH
SSH can be enabled on Raspberry Pi by navigating to the Raspberry Pi Configuration menu and selecting the SSH option. Alternatively, you can enable SSH via the command line by running the following command:
sudo raspi-config
Step 3: Configure Firewall
Setting up a firewall is essential to restrict access to only necessary ports and IP addresses. This minimizes the risk of unauthorized access and ensures that your IoT network remains secure. Carefully configuring firewall rules is a critical step in protecting your devices from potential threats.
Enabling Remote Access
Once SSH is properly configured, you can enable remote access to your Raspberry Pi. This feature allows you to manage your IoT devices from anywhere in the world, providing convenience and flexibility for both personal and professional use.
Using Port Forwarding
Port forwarding enables external devices to connect to your Raspberry Pi by mapping a public port to a private IP address. While this feature enhances accessibility, it is important to exercise caution when setting up port forwarding to avoid exposing your network to potential threats. Proper configuration and monitoring are essential to maintaining security.
Dynamic DNS Services
Dynamic DNS (DDNS) services allow you to access your Raspberry Pi using a domain name instead of an IP address. This is particularly useful if your Internet Service Provider (ISP) assigns dynamic IP addresses. DDNS simplifies remote access by providing a consistent and easy-to-remember address for your device.
Essential Tools for Download and Setup
To facilitate the setup process, consider using the following tools, which are designed to streamline the installation and configuration of your Raspberry Pi:
Etcher
Etcher simplifies the process of writing Raspberry Pi OS images to SD cards. It ensures error-free installations and saves time by automating the writing process. With its user-friendly interface, Etcher is an invaluable tool for both beginners and experienced users.
Putty
Putty is a popular SSH client for Windows users, providing a straightforward interface for connecting to remote devices via SSH. Its simplicity and reliability make it a go-to choice for managing Raspberry Pi and other remote systems.
WinSCP
WinSCP is a secure file transfer client that supports SCP and SFTP protocols. It is ideal for transferring files between your local machine and Raspberry Pi, ensuring that your data remains protected during transmission. WinSCP's intuitive interface makes it easy to use for users of all skill levels.
Best Practices for Security
Implementing best practices is essential for maintaining the security of your IoT devices. By following these guidelines, you can enhance the protection of your network and data:
Regular Updates
Keep your Raspberry Pi and all connected devices updated with the latest software and firmware versions. Regular updates ensure that security vulnerabilities are addressed promptly, reducing the risk of attacks.
Strong Passwords
Use strong, unique passwords for all accounts and avoid reusing passwords across multiple platforms. Strong passwords are a critical line of defense against unauthorized access and should be a priority for all users.
Public Key Authentication
Enable public key authentication for SSH to eliminate the need for passwords and reduce the risk of brute-force attacks. This method provides an additional layer of security by requiring a private key for access, making it significantly more difficult for attackers to gain unauthorized access.
Troubleshooting Common Issues
Even with careful planning, issues may arise during setup. Below are some common problems and their solutions to help you resolve any difficulties you may encounter:
SSH Connection Refused
This error typically occurs when SSH is not enabled or the firewall blocks the connection. Verify SSH settings and check firewall rules to ensure that the necessary ports are open and accessible. Troubleshooting these settings can help resolve the issue and restore connectivity.
Unable to Access Raspberry Pi
If you are unable to access your Raspberry Pi remotely, ensure that port forwarding is correctly configured and that the DDNS service is functioning properly. Double-check all settings and test the connection to identify and resolve any configuration errors.
Conclusion and Next Steps
Securing IoT devices using P2P SSH on a Raspberry Pi is a powerful and effective way to protect your network and data. By following the steps outlined in this guide, you can establish a robust and secure connection for your remote IoT projects, ensuring that your devices remain safe from potential threats. We encourage readers to share their experiences and ask questions in the comments section below. Additionally, explore other articles on our site to deepen your understanding of IoT security and related technologies.
References: