In the fast-paced world of evolving technology, leveraging the best remote IoT device SSH tools has become an indispensable strategy for both businesses and individuals. Securely accessing and managing IoT devices from a distance has transformed how we interact with technology, offering not only greater convenience but also significantly improving the efficiency and reliability of IoT systems. This guide will explore how Secure Shell (SSH) technology plays a pivotal role in safeguarding data transmission and ensuring secure access to IoT devices.
As the Internet of Things (IoT) continues to expand its reach, the importance of secure and reliable remote access solutions has reached unprecedented heights. SSH, or Secure Shell, ensures that the data exchanged between connected devices remains protected from unauthorized access. This article will delve into the top remote IoT device SSH solutions available, highlighting their key features, benefits, and potential applications in various industries.
Whether you are a tech enthusiast, a business owner, or an IT professional, understanding the best remote IoT device SSH solutions can enhance your ability to manage and secure your IoT infrastructure. Join us as we explore this vital topic and uncover the tools that empower you to stay ahead in the dynamic realm of technology.
Read also:Jason Momoa Height
Table of Contents:
- Understanding Remote IoT Device SSH
- The Importance of Remote SSH for IoT Devices
- The Evolution of SSH Technology
- Top Remote IoT Device SSH Solutions
- Key Benefits of Using SSH for IoT Devices
- Security Best Practices for Remote IoT Device SSH
- Implementing SSH for Remote IoT Devices
- Emerging Trends in Remote IoT Device SSH
- Addressing Common Challenges in SSH Implementation
- Conclusion and Next Steps
Understanding Remote IoT Device SSH
Remote IoT device SSH refers to the utilization of Secure Shell protocols to establish encrypted communication channels between IoT devices and remote users. This cutting-edge technology ensures that sensitive data remains protected during transmission, even when accessed from remote locations. As IoT devices become increasingly integrated into everyday operations, the demand for secure remote access solutions has never been more critical.
The most advanced remote IoT device SSH solutions offer a plethora of features, including robust encryption, secure authentication mechanisms, and seamless data transfer capabilities. These tools cater to the diverse needs of businesses and individuals who rely heavily on IoT technology for applications ranging from smart home systems to industrial automation solutions.
By embracing the best remote IoT device SSH practices, users can fortify the security and reliability of their IoT infrastructure, leading to enhanced performance and peace of mind in an interconnected world.
The Importance of Remote SSH for IoT Devices
SSH serves as a secure conduit for remote access to IoT devices, ensuring that unauthorized entities cannot intercept or tamper with sensitive data. This is particularly crucial in industries where data security is non-negotiable, such as healthcare, finance, and manufacturing. SSH not only protects data but also offers several advantages over traditional remote access methods, including:
- Encryption: SSH employs advanced encryption algorithms to safeguard data during transmission.
- Authentication: Users must verify their identity before gaining access to IoT devices, reducing the likelihood of unauthorized access.
- Command Execution: SSH empowers users to execute commands on remote devices, simplifying management and maintenance processes.
By adopting the best remote IoT device SSH solutions, organizations can ensure the security, reliability, and efficiency of their IoT systems while maintaining operational excellence.
Read also:Miranda Richardson
The Evolution of SSH Technology
SSH, or Secure Shell, was first introduced in 1995 by Tatu Ylönen, a researcher at the Helsinki University of Technology. Originally designed as a secure alternative to less reliable remote access protocols like Telnet and rlogin, SSH quickly gained traction due to its robust security features. Over the years, SSH has undergone significant advancements, evolving into a cornerstone of modern cybersecurity with a multitude of versions and implementations.
Today, SSH is indispensable across various industries, from IT to healthcare, providing secure remote access to servers, devices, and other critical systems. Its versatility and reliability have cemented its position as a fundamental component of secure digital infrastructure.
Data and Biodata of SSH Technology:
| Parameter | Details |
|---|---|
| Creator | Tatu Ylönen |
| Year of Creation | 1995 |
| Original Purpose | Secure remote access to replace Telnet and rlogin |
| Current Applications | Secure access to servers, IoT devices, and other systems |
Top Remote IoT Device SSH Solutions
With a myriad of SSH solutions available, selecting the best remote IoT device SSH option can be challenging. Below, we highlight three leading solutions that excel in terms of security, functionality, and ease of use.
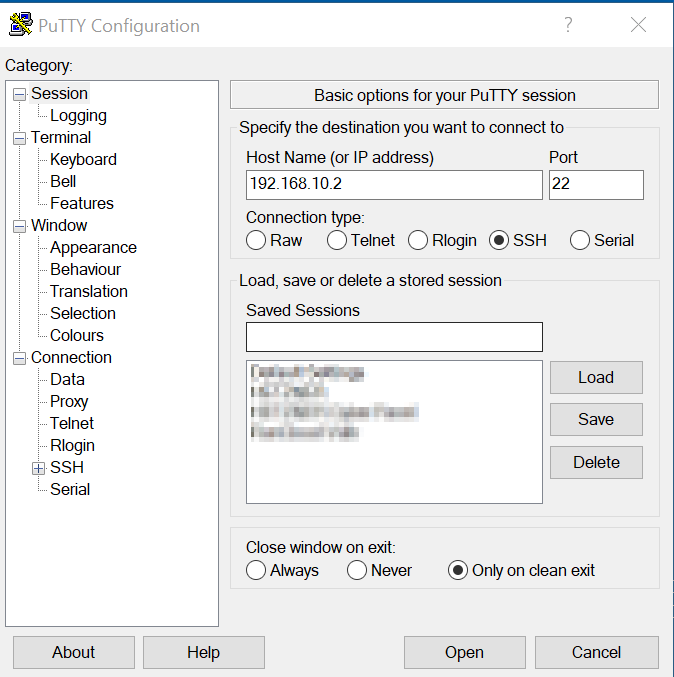
Solution 1: SSH Client Applications
An SSH client is a software application that facilitates secure connections to remote IoT devices. Popular SSH clients include PuTTY, OpenSSH, and Bitvise. These tools offer an array of features, such as encryption, authentication, and command execution, making them indispensable for managing IoT devices remotely. Their user-friendly interfaces and robust capabilities cater to both novice and experienced users alike.
Solution 2: Secure Shell Servers
A Secure Shell server is a server-side application that enables remote access to IoT devices via SSH. Notable Secure Shell servers include OpenSSH Server and Dropbear SSH. These servers provide comprehensive security features, such as key-based authentication and encryption, ensuring that data remains secure during transmission. Their flexibility and reliability make them ideal for securing IoT ecosystems.
Solution 3: Cloud-Based SSH Platforms
Cloud-based SSH solutions, such as AWS Systems Manager and Google Cloud SSH, offer scalable and adaptable options for managing IoT devices remotely. These platforms incorporate enterprise-grade security features, including multi-factor authentication and encryption, making them suitable for large-scale IoT deployments. Their seamless integration with cloud environments enhances the efficiency and scalability of IoT operations.
Key Benefits of Using SSH for IoT Devices
Implementing SSH for remote IoT device management delivers a multitude of advantages, including:
- Enhanced Security: SSH ensures that data remains secure during transmission, minimizing the risk of unauthorized access.
- Improved Efficiency: SSH empowers users to execute commands and manage devices remotely, streamlining maintenance and troubleshooting processes.
- Cost-Effectiveness: Many SSH solutions are open-source or budget-friendly, making them accessible to businesses of all sizes and budgets.
By embracing the best remote IoT device SSH solutions, organizations can achieve greater security, efficiency, and cost savings in their IoT operations, ensuring long-term success in a rapidly evolving digital landscape.
Security Best Practices for Remote IoT Device SSH
While SSH provides a secure method for remote access, adhering to best practices is essential for maximizing protection. Some critical security considerations include:
- Key-Based Authentication: Utilize strong, unique keys for authentication instead of passwords to mitigate the risk of brute-force attacks.
- Regular Updates: Keep SSH clients and servers updated with the latest security patches to address vulnerabilities promptly.
- Network Segmentation: Isolate IoT devices on a dedicated network to minimize the risk of unauthorized access and potential breaches.
By following these security best practices, users can enhance the security of their remote IoT device SSH implementations, safeguarding their digital infrastructure against emerging threats.
Implementing SSH for Remote IoT Devices
Deploying SSH for remote IoT device management involves several critical steps, including:
- Installing SSH Client/Server: Install an appropriate SSH client or server on your system, depending on your specific requirements and objectives.
- Configuring SSH Settings: Customize SSH settings, such as port numbers, authentication methods, and encryption algorithms, to align with your security needs and operational goals.
- Testing the Connection: Verify the functionality and security of the SSH connection to ensure seamless and secure communication between devices.
Following these steps can help you successfully implement SSH for remote IoT device management, fortifying the security and reliability of your IoT infrastructure.
Emerging Trends in Remote IoT Device SSH
As IoT technology continues to evolve, so too will the methods used to secure remote access. Future trends in remote IoT device SSH may include:
- Quantum Encryption: The advent of quantum encryption technologies promises to deliver unprecedented security for SSH connections, safeguarding data against even the most sophisticated cyber threats.
- Artificial Intelligence: AI-driven security tools may enhance SSH's ability to detect and respond to potential threats in real-time, ensuring proactive protection for IoT ecosystems.
- Blockchain Integration: Blockchain technology could facilitate the creation of decentralized SSH systems, further enhancing security, reliability, and transparency in IoT operations.
By staying informed about these emerging trends, users can ensure that their remote IoT device SSH implementations remain at the forefront of cybersecurity innovation.
Addressing Common Challenges in SSH Implementation
While SSH offers numerous benefits for remote IoT device management, several challenges can arise. Some common challenges and their solutions include:
- Challenge: Limited bandwidth for remote access.
Solution: Employ compression techniques to minimize the amount of data transmitted during SSH sessions, optimizing performance and efficiency. - Challenge: Insufficient user training.
Solution: Develop comprehensive training programs to ensure that users are well-versed in SSH best practices, empowering them to leverage the technology effectively. - Challenge: Compatibility issues with certain devices.
Solution: Utilize universal SSH clients and servers that support a wide range of devices and operating systems, ensuring seamless integration across diverse IoT ecosystems.
By addressing these challenges proactively, users can maximize the effectiveness of their remote IoT device SSH implementations, driving success in an interconnected world.
Conclusion and Next Steps
In summary, the best remote IoT device SSH solutions provide a secure and reliable method for managing IoT devices remotely. By leveraging these tools, organizations can enhance the security, efficiency, and cost-effectiveness of their IoT operations. As the IoT landscape continues to evolve, staying informed about emerging trends and best practices will be essential for maintaining a competitive edge in the digital era.
We encourage readers to take the following steps:
- Explore the SSH solutions discussed in this article to identify the one that best aligns with your needs and objectives.
- Adopt security best practices to ensure the maximum protection of your remote IoT device SSH implementations, safeguarding your digital infrastructure against potential threats.
- Stay updated on the latest trends and developments in the field of IoT security to remain at the forefront of innovation