Establishing a secure and efficient remote connection to your Raspberry Pi, even when it's protected by a firewall, can seem daunting at first. However, with the right strategies and tools, this process becomes straightforward and secure. This guide will walk you through essential steps, offering clear instructions and expert advice to simplify the setup of a reliable remote connection to your Raspberry Pi.
In today's tech-driven world, whether you're a beginner or an advanced user, knowing how to connect to your Raspberry Pi from anywhere is crucial. This article will provide detailed instructions, practical tips, and expert insights to ensure seamless connectivity without compromising on security or performance. By the end of this guide, you'll have a thorough understanding of the available methods, necessary tools, and best practices for remote access.
Let’s delve into the details and empower you to connect to your Raspberry Pi remotely with confidence and security.
Read also:Lola Shark Tale
Table of Contents
- Introduction to Remote Access
- Raspberry Pi Overview
- Firewall Challenges
- Methods for Remote Connect
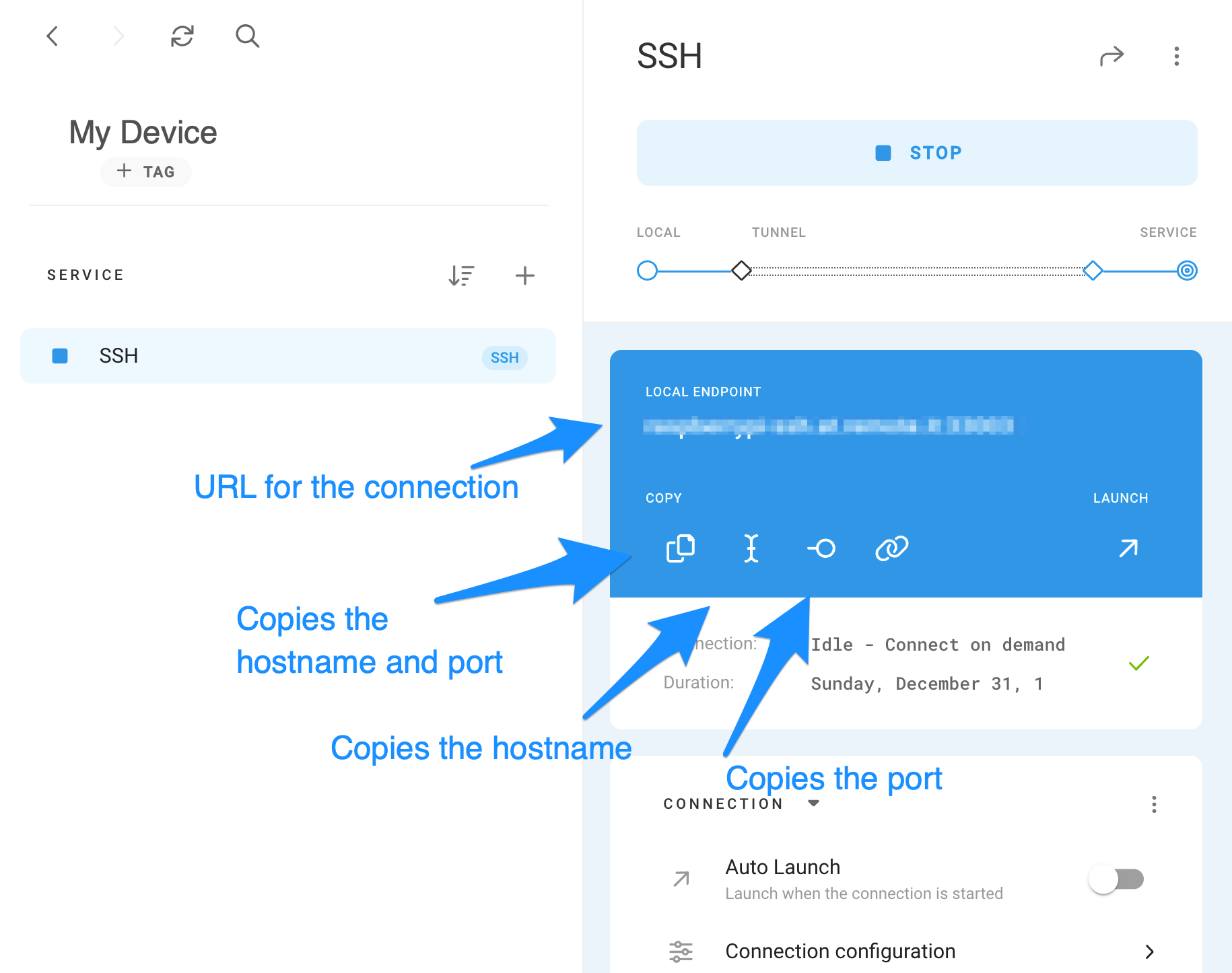
- Setting Up SSH
- Configuring Port Forwarding
- Using a VPN
- Security Best Practices
- Troubleshooting Tips
- Conclusion
Understanding the Fundamentals of Remote Access
Remote access enables you to control and manage devices or systems from a distant location. In an increasingly interconnected world, being able to connect to your Raspberry Pi remotely is not just convenient but essential for managing projects, automating tasks, and monitoring systems effectively. However, when your Raspberry Pi is shielded by a firewall, establishing a secure connection can present challenges.
This section will explore the foundational principles of remote access, emphasizing its importance and the potential obstacles you may face when connecting to a Raspberry Pi behind a firewall. Gaining a solid understanding of these basics will empower you to make informed decisions about the most effective methods for remote access.
Exploring the Raspberry Pi: A Versatile Computing Solution
The Raspberry Pi has revolutionized the tech landscape with its compact size, affordability, and versatility. This credit-card-sized computer has captured the interest of hobbyists, educators, and professionals alike. Its ability to run a wide range of applications, from home automation systems to advanced data processing, makes it an invaluable tool.
For users who require remote access to their Raspberry Pi, ensuring secure connectivity is critical. Thanks to its flexibility, the Raspberry Pi supports various methods for remote access. However, each method comes with its own set of considerations and requirements. This guide will help you navigate these options effectively.
Navigating Firewall Challenges
A firewall serves as a critical component of network security, monitoring and controlling incoming and outgoing network traffic based on established security protocols. While firewalls are essential for safeguarding your network, they can sometimes hinder remote access efforts.
When your Raspberry Pi is situated behind a firewall, you might encounter issues such as restricted ports, blocked IP addresses, and limited access to specific services. This section will examine common challenges and provide strategies to overcome them, ensuring you can maintain a secure and reliable connection to your device.
Read also:Naviyd Ely Raymond
Effective Methods for Remote Connection
SSH Tunneling: A Secure and Reliable Option
SSH (Secure Shell) tunneling stands out as one of the most secure and widely adopted methods for remote access. It facilitates an encrypted connection between your local machine and the Raspberry Pi, safeguarding your data during transmission.
- Begin by enabling SSH on your Raspberry Pi.
- Generate SSH keys to enhance authentication security.
- Establish a secure connection using SSH commands tailored to your setup.
With SSH tunneling, you can enjoy a robust and encrypted connection, ensuring your data remains protected from unauthorized access.
Ngrok: Simplifying Remote Access
Ngrok is a popular tool designed to expose a local server behind a NAT or firewall to the internet. It provides a secure tunnel to your Raspberry Pi without requiring complex configurations or additional software downloads.
Using Ngrok, you can effortlessly access your Raspberry Pi from anywhere globally. This section will guide you through the setup process, highlighting its advantages and simplifying the steps to integrate it into your workflow.
Streamlining SSH Setup on Your Raspberry Pi
Setting up SSH on your Raspberry Pi is a relatively simple process that involves enabling the SSH service and configuring it for remote access. Follow these steps to establish a secure connection:
- Activate SSH on your Raspberry Pi using the Raspberry Pi Configuration tool.
- Create SSH keys to authenticate securely without relying on passwords.
- Adjust the SSH server settings to align with your specific needs and security preferences.
Once SSH is properly configured, you can connect to your Raspberry Pi remotely using a terminal or SSH client, ensuring seamless and secure access.
Configuring Port Forwarding for Enhanced Connectivity
Port forwarding is a technique that redirects communication requests from one address and port number combination to another. When your Raspberry Pi resides behind a firewall, configuring port forwarding on your router can facilitate remote access.
This section will offer detailed, step-by-step instructions for setting up port forwarding on common router models. Additionally, we'll discuss best practices for securing your ports and minimizing potential security risks, ensuring your network remains protected while enabling remote access.
Leveraging a VPN for Secure Remote Access
A Virtual Private Network (VPN) establishes a secure, encrypted connection between your device and a remote network. By utilizing a VPN, you can bypass firewall restrictions and access your Raspberry Pi as though you were on the same local network.
This section will explore the advantages of using a VPN for remote access, recommend reliable VPN providers, and provide setup instructions to connect your Raspberry Pi to a secure network. Discover how a VPN can enhance both the security and accessibility of your Raspberry Pi.
Prioritizing Security: Best Practices for Remote Access
Security must remain a top priority when connecting to your Raspberry Pi remotely. Here are some best practices to ensure your connection remains secure:
- Implement strong, unique passwords for all accounts to deter unauthorized access.
- Enable two-factor authentication (2FA) wherever possible for an added layer of protection.
- Regularly update your Raspberry Pi's software and firmware to patch vulnerabilities.
- Restrict access to trusted IP addresses to minimize potential threats.
Adhering to these practices will fortify your Raspberry Pi against unauthorized access and potential security breaches.
Addressing Common Issues: Troubleshooting Tips
Even with meticulous planning and setup, challenges can arise when connecting to your Raspberry Pi remotely. This section will offer troubleshooting tips for common problems, such as:
- Connection timeouts due to network instability or incorrect configurations.
- Authentication failures stemming from incorrect credentials or misconfigured settings.
- Firewall blocks preventing communication between your local machine and the Raspberry Pi.
By addressing these issues systematically, you can resolve most connectivity problems and ensure a smooth, reliable remote access experience.
Conclusion: Simplifying Remote Access to Your Raspberry Pi
Connecting to your Raspberry Pi remotely, even when it's behind a firewall, doesn't have to be an intimidating task. By leveraging the right tools and techniques, you can establish a secure and dependable connection without the need for unnecessary software downloads.
This article has explored various methods for remote access, including SSH tunneling, Ngrok, port forwarding, and VPNs. We've also discussed security best practices and troubleshooting tips to help you overcome common challenges. With this knowledge, you're well-equipped to manage your Raspberry Pi remotely with confidence and efficiency.
We invite you to share your thoughts and experiences in the comments section below. If you found this article helpful, please consider sharing it with others who may benefit from it. For further guidance and tutorials, explore our other articles on the site and expand your Raspberry Pi expertise.